No magic. Just logic.
Products, websites, and apps — start to finish.
Design‑to‑code builds with a security‑first mindset. I ship fast, keep pixels aligned, and care about outcomes.
Trusted by engineers from








From discovery to deployment — practical craftsmanship with a product mindset.
System and Method for Detecting CyberAttacks Impersonating Legitimate Sources.
Explore work →ML based Phishing Detection Engine based on URL & HTML Models
Explore work →Ranging from drive-by detection, phishing detection, IDS/IPS (Snort, different AV vendors)
Explore work →AWS stack to handle millions of URLs daily using numerous AWS services e.g. S3, CloudWatch, ElastiCache, CloudFormation, Lambdas
Explore work →Amalgamation of hardware & software setup to evaluate current understanding of an AV product
Explore work →Took initiative to capture worldwide malicious HTTP traffic with a target of zero‑day attacks, which eventually covered the gap
Explore work →
Automated workflows within a SOAR platform that execute predefined sequences of actions to handle security incidents.
Explore work →
Process of connecting two or more software applications using their Application Programming Interfaces.
Explore work →
Execution of various projects with standard CI/CD guidelines.
Explore work →
Web application & API white‑ and black‑box penetration testing
Explore work →
State‑of‑the‑art technique that outperforms most IDS/IPS solutions and works well with encrypted traffic
Explore work →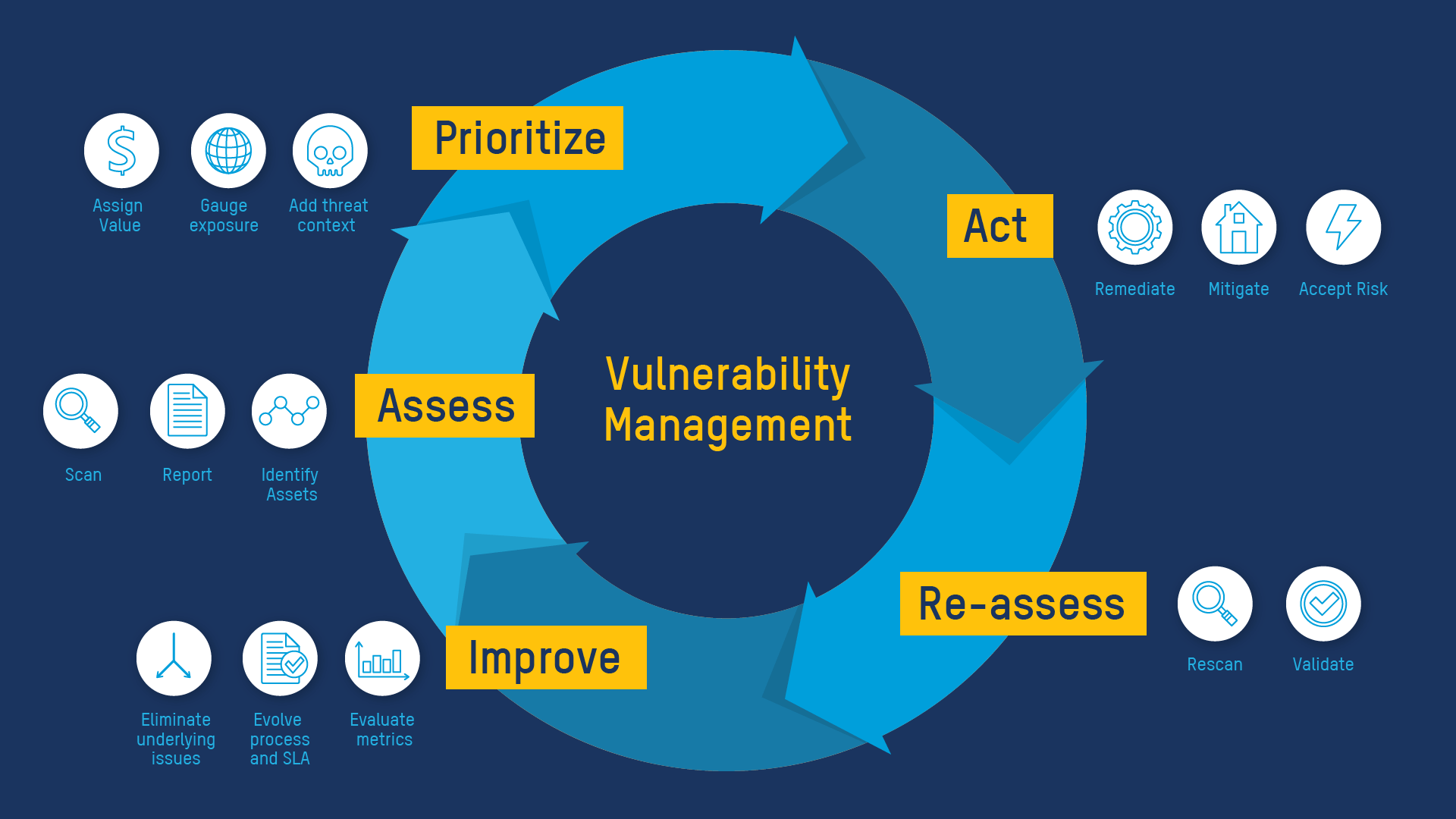
Vulnerability/CVE hunting not only in applications or gateways, but in core protocol stacks with proactive coverage
Explore work →Executive leadership, security expertise, and proven accomplishments.
Send a note and we will reply within 24 hours. Prefer email or a quick call?.

Restructured IA, accessibility-first UI, and faster paths for appointment tasks.
Streaming events, triage queues, and actionable insights for SOC teams.
Django

Checkout conversion +24%, Core Web Vitals in the green, and a sleek, modern, trustworthy, cohesive brand feel.